Part 1: Introduction to Exploit Development -
Hack Like a Pro: How to Build Your Own Exploits,
Part 1: Introduction to Exploit Development -
Exploit writing tutorial: Part 1 - Computer
Exploit writing tutorial part 1: Stack Based Overflows |
Writing an Exploit - Metasploit Unleashed -
 Hack Like a Pro: How to Build Your Own Exploits,
Jan 2015 Developing your own exploits requires considerable knowledge and skill, we will build a simple buffer overflow to demonstrate how a buffer
Analyzing and Writing a Local Exploit - InfoSec
So far, in the previous articles, we learnt how to exploit an application remotely We ran the Python script directly on the Machine B, which was the attacker
Exploit writing tutorial: Part 1 - Computer
In this part of our exploit writing tutorial, we will concentrate on how we can fuzz an application to write an exploit Fuzzing is a very interesting research oriented
How to get started with writing an exploit
The real kung-fu behind exploit development isn t actually about which language you choose to build it, it s about your precise understanding of how an input is
Writing an Exploit - Metasploit Unleashed -
If we look at the source, we can see how this function is called Next up, writing an exploit and getting a shell with what we ve learned about our code
Hack Like a Pro: How to Build Your Own Exploits,
Jan 2015 Developing your own exploits requires considerable knowledge and skill, we will build a simple buffer overflow to demonstrate how a buffer
Analyzing and Writing a Local Exploit - InfoSec
So far, in the previous articles, we learnt how to exploit an application remotely We ran the Python script directly on the Machine B, which was the attacker
Exploit writing tutorial: Part 1 - Computer
In this part of our exploit writing tutorial, we will concentrate on how we can fuzz an application to write an exploit Fuzzing is a very interesting research oriented
How to get started with writing an exploit
The real kung-fu behind exploit development isn t actually about which language you choose to build it, it s about your precise understanding of how an input is
Writing an Exploit - Metasploit Unleashed -
If we look at the source, we can see how this function is called Next up, writing an exploit and getting a shell with what we ve learned about our code
 Best books, tutorials and courses to learn about exploit
Jan 2016 exploit-writing-tutorial-part-1- How to exploit Windows kernel memory pool by SoBeIt [2005]
Part 1: Introduction to Exploit Development -
In general when we write an exploit we need to find an overflow in a program This is a bit simplistic but it should give you a basic idea of how exploits work
Writing Reverse TCP Exploit - InfoSec Resources -
We assume that readers have enough knowledge about how to crash an echo server program and about identifying the return address position by manipulating
Hack Like a Pro: How to Build Your Own Exploits,
Dec 2014 As many of you know, soon after an exploit is found in the wild, software In future tutorials, we will be learning how to manipulate and use these Hack Like a Pro: How to Build Your Own Exploits, Part 2 (Writing a Simple
How to get started with writing an exploit
The real kung-fu behind exploit development isn t actually about which language you choose to build it, it s about your precise understanding of how an input is
Best books, tutorials and courses to learn about exploit
Jan 2016 exploit-writing-tutorial-part-1- How to exploit Windows kernel memory pool by SoBeIt [2005]
Part 1: Introduction to Exploit Development -
In general when we write an exploit we need to find an overflow in a program This is a bit simplistic but it should give you a basic idea of how exploits work
Writing Reverse TCP Exploit - InfoSec Resources -
We assume that readers have enough knowledge about how to crash an echo server program and about identifying the return address position by manipulating
Hack Like a Pro: How to Build Your Own Exploits,
Dec 2014 As many of you know, soon after an exploit is found in the wild, software In future tutorials, we will be learning how to manipulate and use these Hack Like a Pro: How to Build Your Own Exploits, Part 2 (Writing a Simple
How to get started with writing an exploit
The real kung-fu behind exploit development isn t actually about which language you choose to build it, it s about your precise understanding of how an input is
 Writing Reverse TCP Exploit - InfoSec Resources -
We assume that readers have enough knowledge about how to crash an echo server program and about identifying the return address position by manipulating
How to get started with writing an exploit
The real kung-fu behind exploit development isn t actually about which language you choose to build it, it s about your precise understanding of how an input is
Exploit writing tutorial part 1: Stack Based Overflows |
Jul 2009 How can you use vulnerability information to build your own exploit? Ever since I ve started this blog, writing a basic tutorial about writing buffer
Part 1: Introduction to Exploit Development -
In general when we write an exploit we need to find an overflow in a program This is a bit simplistic but it should give you a basic idea of how exploits work
Hack Like a Pro: How to Build Your Own Exploits,
Dec 2014 As many of you know, soon after an exploit is found in the wild, software In future tutorials, we will be learning how to manipulate and use these Hack Like a Pro: How to Build Your Own Exploits, Part 2 (Writing a Simple
Writing Reverse TCP Exploit - InfoSec Resources -
We assume that readers have enough knowledge about how to crash an echo server program and about identifying the return address position by manipulating
How to get started with writing an exploit
The real kung-fu behind exploit development isn t actually about which language you choose to build it, it s about your precise understanding of how an input is
Exploit writing tutorial part 1: Stack Based Overflows |
Jul 2009 How can you use vulnerability information to build your own exploit? Ever since I ve started this blog, writing a basic tutorial about writing buffer
Part 1: Introduction to Exploit Development -
In general when we write an exploit we need to find an overflow in a program This is a bit simplistic but it should give you a basic idea of how exploits work
Hack Like a Pro: How to Build Your Own Exploits,
Dec 2014 As many of you know, soon after an exploit is found in the wild, software In future tutorials, we will be learning how to manipulate and use these Hack Like a Pro: How to Build Your Own Exploits, Part 2 (Writing a Simple
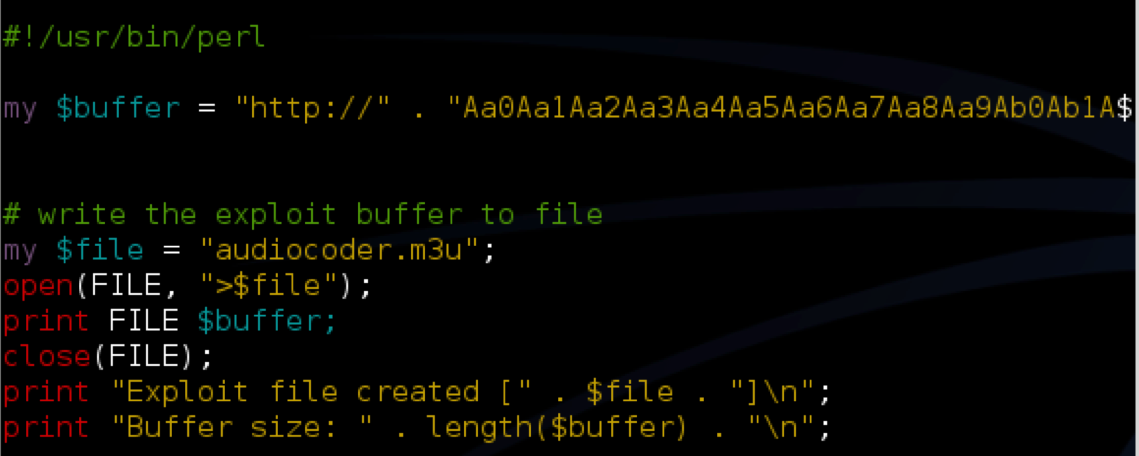 Exploit writing tutorial part 1: Stack Based Overflows |
Jul 2009 How can you use vulnerability information to build your own exploit? Ever since I ve started this blog, writing a basic tutorial about writing buffer
Writing an Exploit - Metasploit Unleashed -
If we look at the source, we can see how this function is called Next up, writing an exploit and getting a shell with what we ve learned about our code
Hack Like a Pro: How to Build Your Own Exploits,
Jan 2015 Developing your own exploits requires considerable knowledge and skill, we will build a simple buffer overflow to demonstrate how a buffer
Part 1: Introduction to Exploit Development -
In general when we write an exploit we need to find an overflow in a program This is a bit simplistic but it should give you a basic idea of how exploits work
Exploit writing tutorial part 1: Stack Based Overflows |
Jul 2009 How can you use vulnerability information to build your own exploit? Ever since I ve started this blog, writing a basic tutorial about writing buffer
Writing an Exploit - Metasploit Unleashed -
If we look at the source, we can see how this function is called Next up, writing an exploit and getting a shell with what we ve learned about our code
Hack Like a Pro: How to Build Your Own Exploits,
Jan 2015 Developing your own exploits requires considerable knowledge and skill, we will build a simple buffer overflow to demonstrate how a buffer
Part 1: Introduction to Exploit Development -
In general when we write an exploit we need to find an overflow in a program This is a bit simplistic but it should give you a basic idea of how exploits work
 Part 1: Introduction to Exploit Development -
In general when we write an exploit we need to find an overflow in a program This is a bit simplistic but it should give you a basic idea of how exploits work
Hack Like a Pro: How to Build Your Own Exploits,
Jan 2015 Developing your own exploits requires considerable knowledge and skill, we will build a simple buffer overflow to demonstrate how a buffer
Exploit writing tutorial part 1: Stack Based Overflows |
Jul 2009 How can you use vulnerability information to build your own exploit? Ever since I ve started this blog, writing a basic tutorial about writing buffer
Hack Like a Pro: How to Build Your Own Exploits,
Dec 2014 As many of you know, soon after an exploit is found in the wild, software In future tutorials, we will be learning how to manipulate and use these Hack Like a Pro: How to Build Your Own Exploits, Part 2 (Writing a Simple
Writing an Exploit - Metasploit Unleashed -
If we look at the source, we can see how this function is called Next up, writing an exploit and getting a shell with what we ve learned about our code
Part 1: Introduction to Exploit Development -
In general when we write an exploit we need to find an overflow in a program This is a bit simplistic but it should give you a basic idea of how exploits work
Hack Like a Pro: How to Build Your Own Exploits,
Jan 2015 Developing your own exploits requires considerable knowledge and skill, we will build a simple buffer overflow to demonstrate how a buffer
Exploit writing tutorial part 1: Stack Based Overflows |
Jul 2009 How can you use vulnerability information to build your own exploit? Ever since I ve started this blog, writing a basic tutorial about writing buffer
Hack Like a Pro: How to Build Your Own Exploits,
Dec 2014 As many of you know, soon after an exploit is found in the wild, software In future tutorials, we will be learning how to manipulate and use these Hack Like a Pro: How to Build Your Own Exploits, Part 2 (Writing a Simple
Writing an Exploit - Metasploit Unleashed -
If we look at the source, we can see how this function is called Next up, writing an exploit and getting a shell with what we ve learned about our code
 How to get started with writing an exploit
The real kung-fu behind exploit development isn t actually about which language you choose to build it, it s about your precise understanding of how an input is
Exploit writing tutorial: Part 1 - Computer
In this part of our exploit writing tutorial, we will concentrate on how we can fuzz an application to write an exploit Fuzzing is a very interesting research oriented
Writing an Exploit - Metasploit Unleashed -
If we look at the source, we can see how this function is called Next up, writing an exploit and getting a shell with what we ve learned about our code
Exploit writing tutorial part 1: Stack Based Overflows |
Jul 2009 How can you use vulnerability information to build your own exploit? Ever since I ve started this blog, writing a basic tutorial about writing buffer
Hack Like a Pro: How to Build Your Own Exploits,
Jan 2015 Developing your own exploits requires considerable knowledge and skill, we will build a simple buffer overflow to demonstrate how a buffer
How to get started with writing an exploit
The real kung-fu behind exploit development isn t actually about which language you choose to build it, it s about your precise understanding of how an input is
Exploit writing tutorial: Part 1 - Computer
In this part of our exploit writing tutorial, we will concentrate on how we can fuzz an application to write an exploit Fuzzing is a very interesting research oriented
Writing an Exploit - Metasploit Unleashed -
If we look at the source, we can see how this function is called Next up, writing an exploit and getting a shell with what we ve learned about our code
Exploit writing tutorial part 1: Stack Based Overflows |
Jul 2009 How can you use vulnerability information to build your own exploit? Ever since I ve started this blog, writing a basic tutorial about writing buffer
Hack Like a Pro: How to Build Your Own Exploits,
Jan 2015 Developing your own exploits requires considerable knowledge and skill, we will build a simple buffer overflow to demonstrate how a buffer
 How to get started with writing an exploit
The real kung-fu behind exploit development isn t actually about which language you choose to build it, it s about your precise understanding of how an input is
Part 1: Introduction to Exploit Development -
In general when we write an exploit we need to find an overflow in a program This is a bit simplistic but it should give you a basic idea of how exploits work
Best books, tutorials and courses to learn about exploit
Jan 2016 exploit-writing-tutorial-part-1- How to exploit Windows kernel memory pool by SoBeIt [2005]
Analyzing and Writing a Local Exploit - InfoSec
So far, in the previous articles, we learnt how to exploit an application remotely We ran the Python script directly on the Machine B, which was the attacker
Hack Like a Pro: How to Build Your Own Exploits,
Jan 2015 Developing your own exploits requires considerable knowledge and skill, we will build a simple buffer overflow to demonstrate how a buffer
Writing an Exploit - Metasploit Unleashed -
If we look at the source, we can see how this function is called Next up, writing an exploit and getting a shell with what we ve learned about our code
How to get started with writing an exploit
The real kung-fu behind exploit development isn t actually about which language you choose to build it, it s about your precise understanding of how an input is
Part 1: Introduction to Exploit Development -
In general when we write an exploit we need to find an overflow in a program This is a bit simplistic but it should give you a basic idea of how exploits work
Best books, tutorials and courses to learn about exploit
Jan 2016 exploit-writing-tutorial-part-1- How to exploit Windows kernel memory pool by SoBeIt [2005]
Analyzing and Writing a Local Exploit - InfoSec
So far, in the previous articles, we learnt how to exploit an application remotely We ran the Python script directly on the Machine B, which was the attacker
Hack Like a Pro: How to Build Your Own Exploits,
Jan 2015 Developing your own exploits requires considerable knowledge and skill, we will build a simple buffer overflow to demonstrate how a buffer
Writing an Exploit - Metasploit Unleashed -
If we look at the source, we can see how this function is called Next up, writing an exploit and getting a shell with what we ve learned about our code
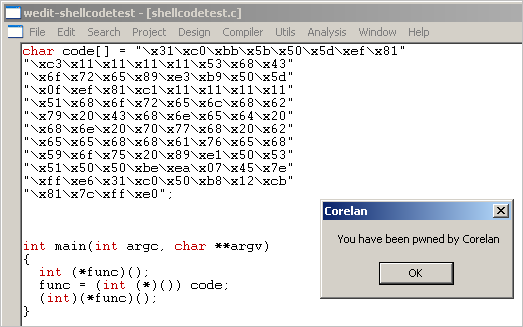 Exploit writing tutorial part 1: Stack Based Overflows |
Jul 2009 How can you use vulnerability information to build your own exploit? Ever since I ve started this blog, writing a basic tutorial about writing buffer
Hack Like a Pro: How to Build Your Own Exploits,
Dec 2014 As many of you know, soon after an exploit is found in the wild, software In future tutorials, we will be learning how to manipulate and use these Hack Like a Pro: How to Build Your Own Exploits, Part 2 (Writing a Simple
Writing an Exploit - Metasploit Unleashed -
If we look at the source, we can see how this function is called Next up, writing an exploit and getting a shell with what we ve learned about our code
Exploit writing tutorial part 1: Stack Based Overflows |
Jul 2009 How can you use vulnerability information to build your own exploit? Ever since I ve started this blog, writing a basic tutorial about writing buffer
Hack Like a Pro: How to Build Your Own Exploits,
Dec 2014 As many of you know, soon after an exploit is found in the wild, software In future tutorials, we will be learning how to manipulate and use these Hack Like a Pro: How to Build Your Own Exploits, Part 2 (Writing a Simple
Writing an Exploit - Metasploit Unleashed -
If we look at the source, we can see how this function is called Next up, writing an exploit and getting a shell with what we ve learned about our code
 Writing an Exploit - Metasploit Unleashed -
If we look at the source, we can see how this function is called Next up, writing an exploit and getting a shell with what we ve learned about our code
Writing Reverse TCP Exploit - InfoSec Resources -
We assume that readers have enough knowledge about how to crash an echo server program and about identifying the return address position by manipulating
How to get started with writing an exploit
The real kung-fu behind exploit development isn t actually about which language you choose to build it, it s about your precise understanding of how an input is
Writing an Exploit - Metasploit Unleashed -
If we look at the source, we can see how this function is called Next up, writing an exploit and getting a shell with what we ve learned about our code
Writing Reverse TCP Exploit - InfoSec Resources -
We assume that readers have enough knowledge about how to crash an echo server program and about identifying the return address position by manipulating
How to get started with writing an exploit
The real kung-fu behind exploit development isn t actually about which language you choose to build it, it s about your precise understanding of how an input is
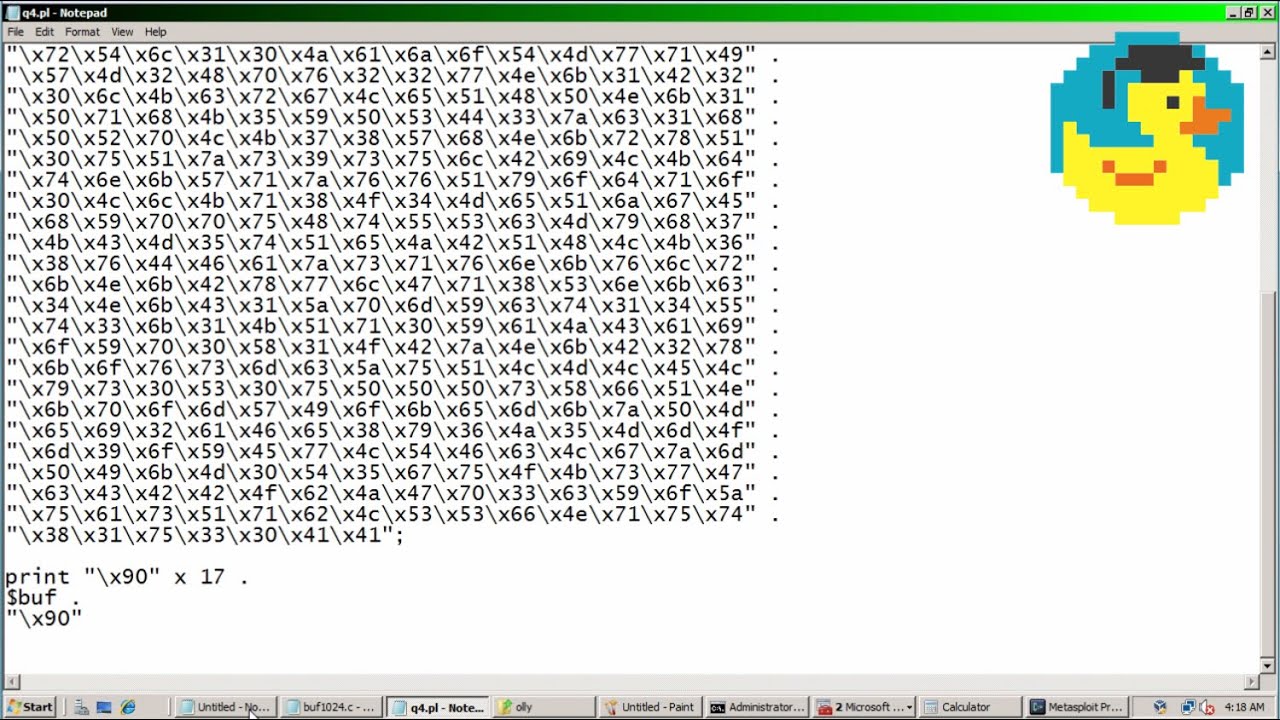 Hack Like a Pro: How to Build Your Own Exploits,
Jan 2015 Developing your own exploits requires considerable knowledge and skill, we will build a simple buffer overflow to demonstrate how a buffer
Exploit writing tutorial part 1: Stack Based Overflows |
Jul 2009 How can you use vulnerability information to build your own exploit? Ever since I ve started this blog, writing a basic tutorial about writing buffer
Part 1: Introduction to Exploit Development -
In general when we write an exploit we need to find an overflow in a program This is a bit simplistic but it should give you a basic idea of how exploits work
Hack Like a Pro: How to Build Your Own Exploits,
Jan 2015 Developing your own exploits requires considerable knowledge and skill, we will build a simple buffer overflow to demonstrate how a buffer
Exploit writing tutorial part 1: Stack Based Overflows |
Jul 2009 How can you use vulnerability information to build your own exploit? Ever since I ve started this blog, writing a basic tutorial about writing buffer
Part 1: Introduction to Exploit Development -
In general when we write an exploit we need to find an overflow in a program This is a bit simplistic but it should give you a basic idea of how exploits work